Know About Spear Phishing Attacks and What Makes It Different From Phishing


In today’s world of digitization, securing your business from phishing attacks have never been more essential. This particular post is going to aware our readers with a trending phishing mechanism named as spear phishing, which is day-by-day spreading without any pause.
What is Spear Phishing Attacks?
This is a kind of social engineering threat, which tricks a victim into exposing sensitive content, installing of malware, or initiate an APT. Hackers try their best to steal confidential information like account credentials, financial records, clients records, etc., from the targeted PC. Usually, the Cybercriminals try to establish a trustworthy relationship with the victim by becoming their employer, friends, an office colleague, or other sorts of tricky methods. They then pretend to be a trustworthy individual in front of the victim, with the intention of gaining confidential records, either through emails or chats. For internet hackers, this is one of the most successful methods to reveal confidential data over the web.
This type of attack is a perfect source for hackers to target large enterprises. Below listed are some of the few examples, which represent how smart social engineering could make a highly-protective business susceptible to spear phishing:
- Spear phishing threats against companies have become common for FBI. They had released an announcement for public service giving warning against the official emails being getting compromised. This incident took place back in 2015 when a technical firm – Ubiquiti suffered from a $46M financial loss only because of spear phishing attack.
- This example of Spear Phishing Attacks is really horrible. In this, the attackers cleverly came in between the ongoing chat messages with extremely customized messages. This clever attitude was not noticed by targeted entities and they assumed that they were chatting continuously with original person. With help of this technique, attackers infiltrated multiple enterprises like Middle Eastern bank, an international sporting company, and the European intellectual services agency.
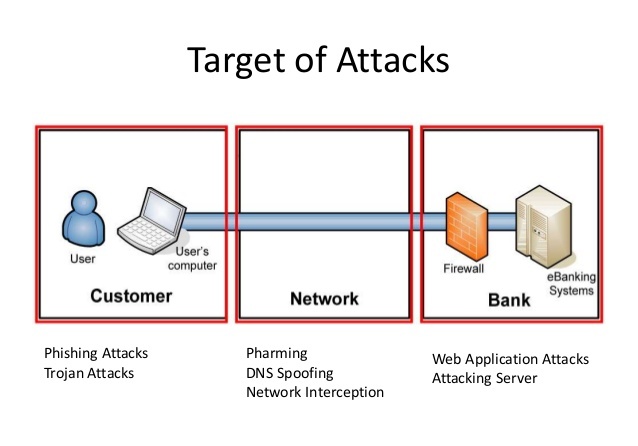
Distinguish Between Phishing and Spear Phishing Attacks
There arises lots of confusion between both of these attacks because both of them aim at gaining confidential data. The term ‘Phishing’ is broader for any efforts to force victims to share their sensitive records like usernames, credit card details, and passwords for malicious causes. Often, the Cybercriminals pretend as if they are a trustworthy entity and create a term with their targeted personalities through phone calls, WhatsApp chats, social media messaging, and emails.
Unlike the spear phishing email threats, phishing cloud attacks are not attempted in a personalized manner. These are sent to a bulk of people simultaneously through web links, email content, or a mail attachment. The major aim of phishing threats is to send a malicious email, which seems normal. This kind of email message is designed in a way that it looks as if it has been mailed from an authentic entity to the huge number of users. Attackers hope that out of 100 at least 50 users will open that malicious link and finally, permit them to enter into one of the PCs of the targeted company.
On the other hand, spear phishing threats target on a particular victim and then, customize the messages to establish a relationship with the victim. This demands for lots of thinking procedure and time to get a successful outcome. Attackers who desire to attempt spear phishing try hard to gain as much personal content about their targeted entities as possible. This kind of observation helps them in making emails look like a legitimate document and to of course increase the overall probability of fooling the recipients. Just because of the personal level attack, it is much more tough to determine spear phishing email threats than to determine phishing threats attempted at a broad level. This is the reason due to which cloud computing security experts consider spear phishing more prevalent in comparison to the phishing threats while performing cloud monitoring.
Best Practices for Spear Phishing Prevention
Following are some common best practices that should be adopted by each and every individual who work online. These measures will help them to be safe from spear phishing:
- Regularly make use of awareness training sessions to educate executives about being extremely vigilant towards the sharing of personal information through social media platforms. For example – It is an easy target for hackers to attack LinkendIn profiles by establishing a trustworthy business relation.
- It is essential to have control over Cyber threats & the Cyber Security Strategy should be implemented at the earliest stage. This will prove an effective technique when one will observe reducing of damages and achieving enterprises back on the ground. Strongly recommend business workers to report a threat and have a sudden action strategy to stem the tide.
- Organizations should make it a regular responsibility of backing up their data in a reliable manner, comprising of SaaS information like G Suite and Office 365. This will help in recovering records rapidly and without any loss, enable enterprises to continue their growth, even if in case threat occurs.
Beware and Be Secure While Working Online
Spear Phishing Attacks are usually caused by threating the emotional level of targeted entities. Before talking to some unknown individual, cloud users are advised to take Spear Phishing preventions. If they find something fishy, immediately give the report to higher authorities. Stay safe and beware with what’s going on in surroundings.