Protect Office 365 From Phishing Attacks


There are several internal threat protection tools provided by Microsoft for Office 365 users. Through this blog, we want to aware the Exchange Online users that they can integrate services and features of Office 365 threat management stack. This enables administrators or tenant users to protect Office 365 from phishing attacks.
What is Phishing Attacks? Protect Office 365 Data from Phishing Attack
The activity in which attackers grab the account credentials, credit card details, and all other secretive information by representing themselves as an authentic entity in the business. They misguide the recipients by making them believe that the email is from a legitimate source. These type of emails comprise of a convincing content, which forces the recipient to take an action for them. There are different occurrence forms of phishing emails like :
- Impersonation: The type of emails are intended in a way that they look as if they came from a known domain, brand, and users.
- Spoofing: This type of emails are designed by attackers in a way that they match the legitimate business.
- Content-Based Attacks: In this type of phishing attack, the virus or attack is appended in the email attachments or weblinks.
This was all about ‘what is phishing attack?’ Now in the further section, you will get to know about the several services to get the protection of Office 365 from phishing attacks through end-to-end method against the recent sophisticated phishing campaigns.
End-to-End Cloud Security
The stack of Microsoft Office 365 threat protection makes the combination of a rich set of features. These features are purposely designed to keep account safe from phishing attacks. Not only for this but, the security team devotes its 100% in detecting and responding to these type of attacks. The services offered by Microsoft are:
- Protect: Setup and configure the security services of Office 365 for keeping users secure
- Defect: If a threat enters the account then, it gets determined with the details where and how the data is impacted.
- Respond: Try to re-mediate the attack or threat of returning back the tenant in ‘safe, no threat’ mode.
Protect
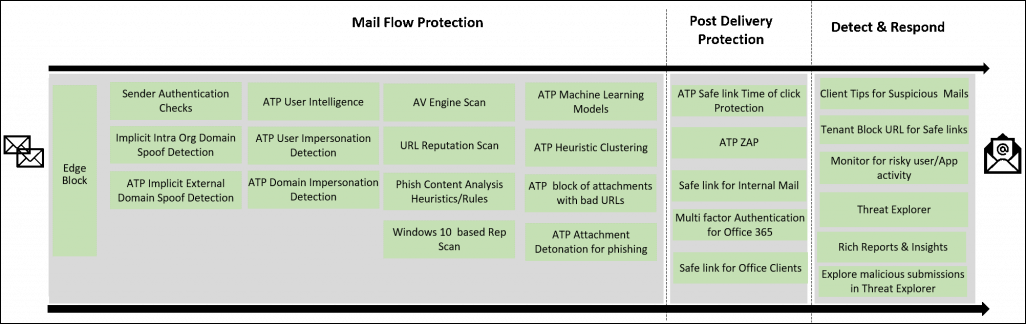
The initial step to protect Office 365 from phishing attacks is deep analysis on the elimination of attack before it harms the entire firm. A rich, comprehensive, multi-layered, and robust solution is offered in the Office 365 to learn about the attack. Microsoft offers an Office 365 threat protection anti-phish stack.
- At the stage of mail-flow protection, all messages have to pass the authentication procedure. This process involves the explicit anti-spoof framework comprising of DKIM, DMARC, and SPF. Each and every email have to pass this implicit authentication, which is built on the extra machine learning models for identifying the email authenticity.
- Anti-impersonation features are launched to flag the highly advanced and targeted spear-phishing emails. The harmful content exists in form of an attachment, a web link, and images. In Office 365 account, these links and attachments are detonated and analyzed for examining the malicious content.
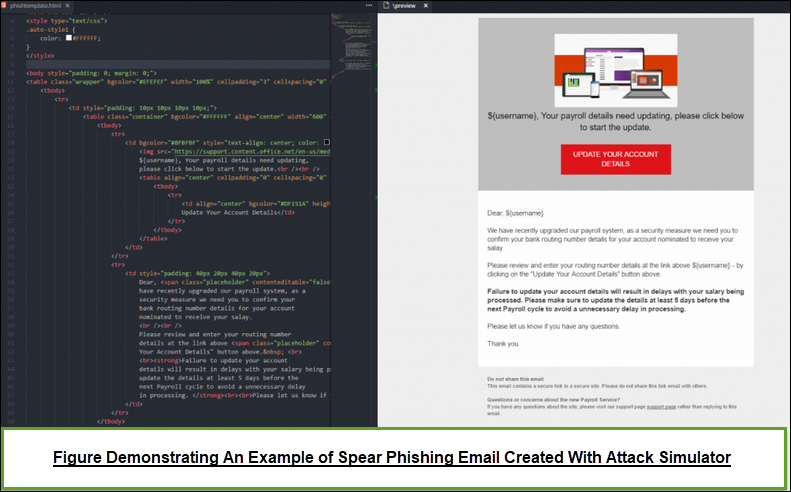
- A new public preview feature named as Attack Simulator is offered by Office 365. Display Name Spear Phishing Attack is one of the initial threat simulations present in the Attack Simulator. The term ‘spear phishing’ is the subset of phishing attacks where the target is on the entire organization / a group/individuals. Well, the Attack Simulator notifies the targeted users and provide them guidance to recognize the phishing emails. This helps them against the protection of Office 365 from phishing attack on time.
Detect
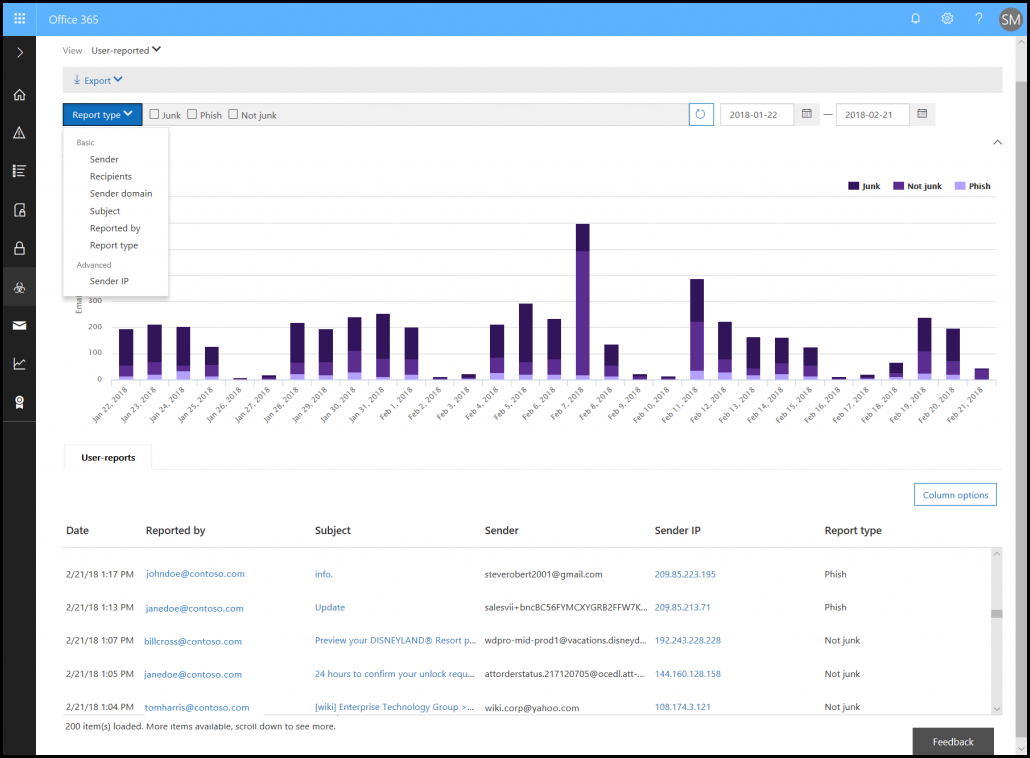
Customers are allowed to have continuous visibility on all malicious emails, which makes their account on target. They can also block them in their Exchange Online tenant. Administrators who are working with ATP will be able to view all the messages, which are marked and submitted by users as the potential threats. An administrator can:
- Determine the email sender
- Total instances of the email
- Total number of users received the mail
The tool that provides the view of messages submitted by users is extremely valuable. It is so because it empowers the security team of an organization by determining the malicious emails and then notifying of the potential threats. A comprehensive view is provided to the security team and administrator to learn about the phishing campaigns in depth. In order to analyze the things in the deeper manner, the user-reported submissions are also emailed to Microsoft.
Respond
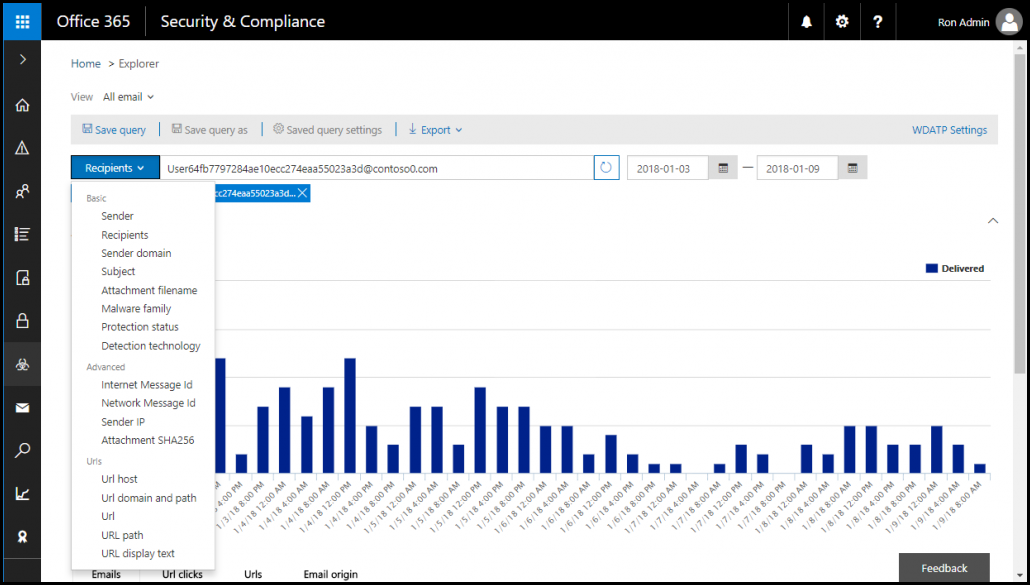
This is the last stage to protect Office 365 from phishing attacks. It involves the use of O365 Threat Intelligence program that allows enterprises to thoroughly investigate, give the response, and cure the attack held on their premises. Many organizations have adopted CASB services whose goal is to keenly focus on cloud storage security and allow business customers to focus on their growth. Not only this much but, they assess the threat impact on the firm. Security administrators and analysts can take help of Threat Explorer feature (availed in Security and Compliance Center) to search for all the instances of potential malicious messages. With the help of this Threat Explorer feature, it is possible to easily identify the malicious content or emails. It provides different filtering as well as searching options like recipient, sender, and other parameters for determining the malicious medium. Administrators can acquire visibility on the email’s sender with the help of user-reported threats view. This is a crucial part of the messages because in general cases, phishing campaign is conducted from a unique email id. The Threat Explorer enables the administrator to filter the data on basis of ‘sender’ to determine whether the emails are sent from one email address or not.
Time to Conclude
Since a long time, Microsoft was dedicated to offering its clients solutions to protect Office 365 from phishing attacks. Since the year 2017, cybercrime came into the hearing on the regular basis that means that crime is also occurring rapidly on the internet. So, it becomes important to focus and put more efforts on enhancing the cloud storage security. This will keep the confidential information safe on the cloud from Cyber threats. Microsoft Office 365 threat protection offers different security techniques that will surely help a business to work in the cloud with no fear. The protection of Office 365 from phishing can lead to safety & security.